BRIAR and the "Ocean of Data"
I was first introduced to Briar (Briarproject.org) at Pierogarnia, a nice bar with Polish food in Wedding, Berlin. Briar is basically a robust messaging app using device-to-device communication, avoiding a central server, and capable of being used as some sort of mesh network to communicate off-internet. While using the Internet, Briar can sync via the Tor network which defends users against traffic analysis, interception and surveillance.
(Arguably), the most lucid article that exists about Briar is by Torsten Grote, responsible for transportr, an android app which I have installed on F-Droid, alongside many others. Torsten has also influenced German policy since he is responsible for the addition of Free Software to the agenda of German's Pirate Party, after his memorandum about a free democratically controlled technological infrastructure was accepted.
Here is his article entitled "Briar – Next Step of The Crypto Messenger Evolution".
Before introducing Briar, he navigates from the old days when we were lucky if we had transport encryption on our stone-edge messengers such as, ICQ to more recent apps providing end-to-end encryption (obviously whatsapp's recent security update by Open wishpers comes to mind) and discusses different types of centralised and decentralised communication architecture on the Internet, including peer-to-peer (as in Briar). Among others, he discusses Open Wishpers's app called Signal, which I use on my phone (despite it drags your battery quite ferociously!)
One of the highlights of the article, and something that I have been thinking for a while, is that when discussing personal privacy, is no longer so much about protecting the interception of information in a one-off communication call but about protecting your metadata. Targeted single interceptions are not so valuable for traffic analysis although it may reveal some specifics. It does not provide the adversaries with a full picture of who you are, what are your patterns of behaviour and with whom do you relate to on your daily routines. It is the protection of your metadata what really matters. The adversary can make use of such valuable overlay of data emerging from your persona for any kind of purposes. A very annoying one is targeted advertising (this is at the core of social networks and browser searches) but of course,
the aforementioned article goes a step further when pointing to the youtube video where a well-known organisation admit that they "kill people based on metadata". However, to contextualise the video comment more, it also makes the point on the fact that such powerful algorythms are clearly not applied to "domestic databases". I understand that the latter refers to metadata collected from normal citizens via social networks and google-like searches. That is good to know...!
Also it suggests where are the legal limits and authorisations for the organisation in terms of what can be done with what is called "the Ocean of Data".
So, normal citizens can rest asured.
Back in 2008 I wanted to investigate how metadata can also be powerful for sound retrieval. Therefore, I constructed a retrieval system based on soundfiles attached metadata which proved to be extremely powerful for the articulation of sound. I used such local retrieval metadata system in the context of an interacive game-audio work called "Ho" a sonic expedition to vietnam.
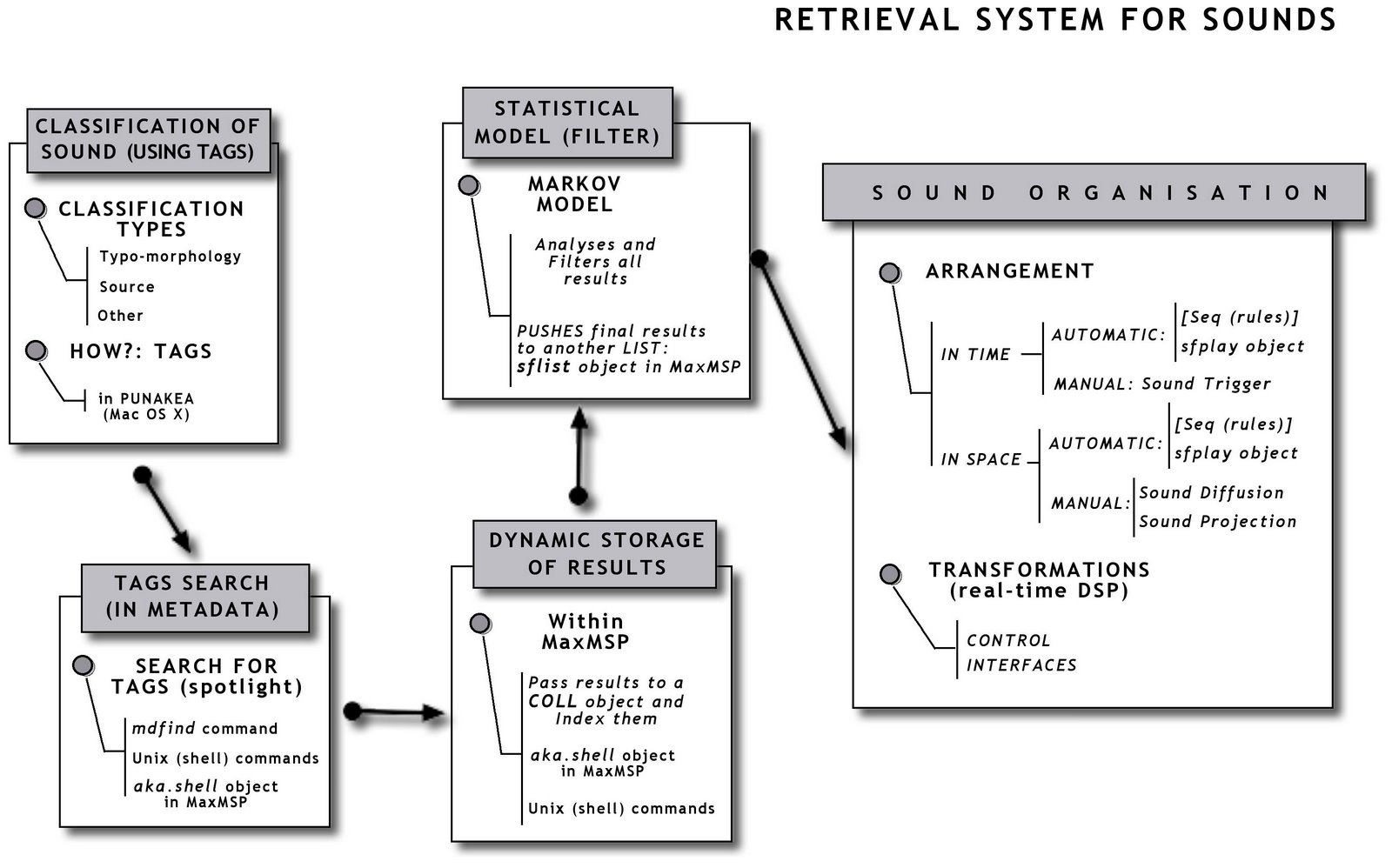
Here is a bit of an explanation of how the metadata is used to retrieve a collection of sounds from MaxMSP using punakea to tag clusters of files.
Retrieving Audio using custom metadata in maxmsp via Blender from Wunderbar Lab Berlin on Vimeo.
This was later called from a number of game-engine events (mostly collisions) taking place in Blender's game-engine (BGE) via OSC (Open Sound Control) protocol. Here is a 2009 test with the integration of both using Python in the BGE. https://vimeo.com/16473899
Now my final question: What if my soundfiles had become aware of the the fact that they are used, behave according to and become organised, due to their metadata? What if they could prevent me (the composer, the adversary) from adding such meta-information to they aural entities? Well, who knows, but I might have to get back to the era of crotchets and quavers to make music!
So, do you fancy building Briar from the source-code? If not, be patient until its public release!